How do cryptocurrencies work?
Decentralized consensus
Price is the least interesting thing about bitcoin.
This is my attempt to explain how a standard cryptocurrency like Bitcoin works. Other cryptocurrencies may diverge on various points, but the fundamentals are the same.
As stated in the introduction, the focus isn’t on technical details, but it’s a tight balance to make between keeping it simple and explaining how cryptocurrencies work. If this chapter is too technical, you can safely skip to the next chapter or just read the summary—it’s not required knowledge.
Summary
The blockchain is a ledger that stores balances. The crucial problem is deciding between double spends (using a coin twice). Cryptocurrencies like Bitcoin use proof-of-work which makes miners expend energy and compete for rewards. This competition between miners is used to resolve double spends and to secure the chain, allowing the winner to extend the blockchain with new transactions that don’t double spend.
What makes it all work is the incentives for the miners to work in the best interest of the network as it’s the most profitable option. The security assumption is that most of the miners are honest and work for profit, otherwise the security model fails and transactions can be reversed.
The ledger
If you want to create a digital currency, you only really need to keep track of how many coins everyone have. For example, your bank might have entries in a ledger like this:
| Person | Swedish krona |
|---|---|
| Sneaky Steve | 7 000 SEK |
| Honest Harry | 1 000 SEK |
When Sneaky Steve wants to send 500 SEK to Honest Harry, the bank simply updates the ledger:
| Person | Swedish krona |
|---|---|
| Sneaky Steve | 6 500 SEK (-500 SEK) |
| Honest Harry | 1 500 SEK (+500 SEK) |
Cryptocurrencies work this way, as well. In fact, the ledger in a cryptocurrency, often referred to as the blockchain, contains the balance of all addresses.
Your keys, your coins
To be able to create a transaction, you need to have the private keys to the address you want to send from. Think of it as a secret password that unlocks your account. This prevents anyone else from stealing your coins, unless, of course, they steal your private key!
It uses public-key cryptography, which allows you to prove you control the private key without sharing the private key itself. Compare it to credit card numbers which act as both a private and public key. See A hitchhiker’s guide to cryptography for more details, but a low-level cryptographic understanding isn’t required to understand how cryptocurrencies work.
Copying a coin & double spending
So far, cryptocurrencies don’t do anything new. The hard problem is: how do you prevent someone from copying a coin, and sending the copies to two different receivers? Couldn’t you just copy the hard drive to copy your coins?
For example, Sneaky Steve wants to buy a computer from Honest Harry and wants to pay with Bitcoin. The computer costs 1 BTC, and the Bitcoin ledger looks like this:
| Address | Bitcoin |
|---|---|
| Sneaky Steve 1 | 1 BTC |
| Sneaky Steve 2 | 0 BTC |
| Honest Harry | 0 BTC |
What Sneaky Steve tries to do is send 1 BTC to the merchant, Honest Harry, and then send a copy of 1 BTC to his other address: Sneaky Steve 2. (It’s possible to have as many addresses as you want—a consequence of the permissionless nature of Bitcoin.)
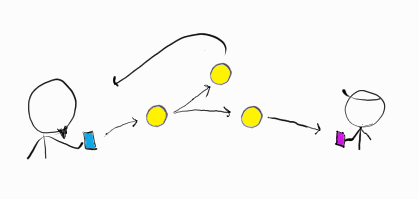
If we didn’t prevent this, the ledger might look like this:
| Address | Bitcoin | Diff |
|---|---|---|
| Sneaky Steve 1 | -1 BTC | (-2 BTC) |
| Sneaky Steve 2 | 1 BTC | (+1 BTC) |
| Honest Harry | 1 BTC | (+1 BTC) |
We copied our coin and printed 1 BTC out of thin air, so now the ledger contains a negative balance. This is a form of double spending—spending the same coin twice.
This isn’t really a problem with physical cash since you can’t just copy gold coins or paper notes. It’s not a problem for banks either since the bank can just deny one or both of the transactions. This is a hard problem for a digital currency that tries to remove the central authority, and this is why before Bitcoin no decentralized digital currency existed.
The Byzantine Generals Problem
To resolve double spending, it’s enough to choose one of the double spending transactions. But how do you do that when there are many unrelated people—and some who want to cheat?
This is the same problem as the Byzantine Generals Problem. Here’s my description of a simple variation:
In the Eastern Roman Empire, also referred to as the Byzantine Empire, several generals surround an enemy city:
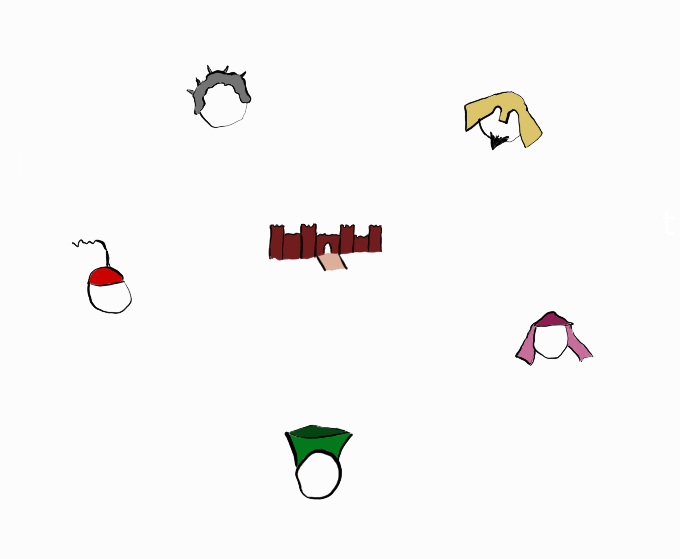
The city is very well-defended and if they attack individually, they will be defeated. So, they will have to work together and coordinate to attack at the same time, or retreat as a unit. Doing nothing is not an option either as they have a limited food supply while the city is waiting for reinforcements.
If they try to act without a majority, they will surely face defeat—they must coordinate.
This would be very easy if they could trust each other. Unfortunately, they cannot trust the messages—either the messenger or the message itself could be replaced—and even some of the generals could be traitors.
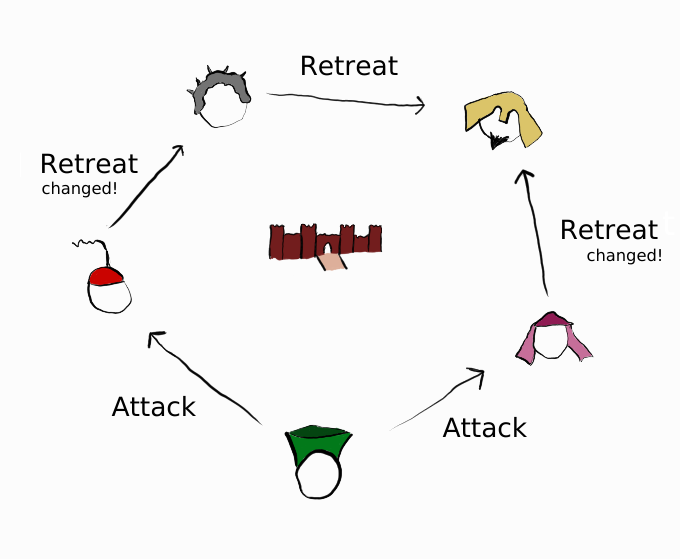
In this simple example, three of the generals now believe that they will attack while two are preparing to retreat. In a more complex scenario, they might receive conflicting messages and notice something is amiss, but they don’t know what’s real and what’s not and cannot decide what to do.
To relate it back to cryptocurrencies, the choice between “attack” and “retreat” is similar to choosing between two transactions in a double spend. You know there are bad actors, but who can you trust?
Sybil attack
You may think most users in the network are honest, so can’t you just ask everyone?
Unfortunately, there’s a serious problem here. As there’s no barrier to participate in the network and no identity control, a single person can have multiple identities:
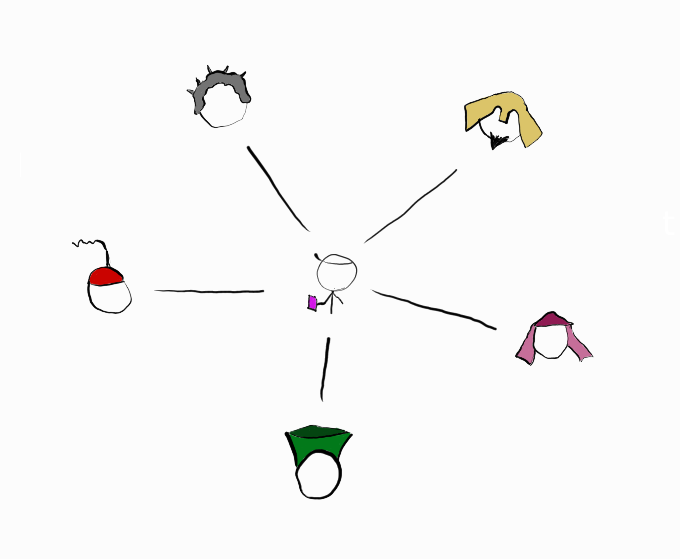
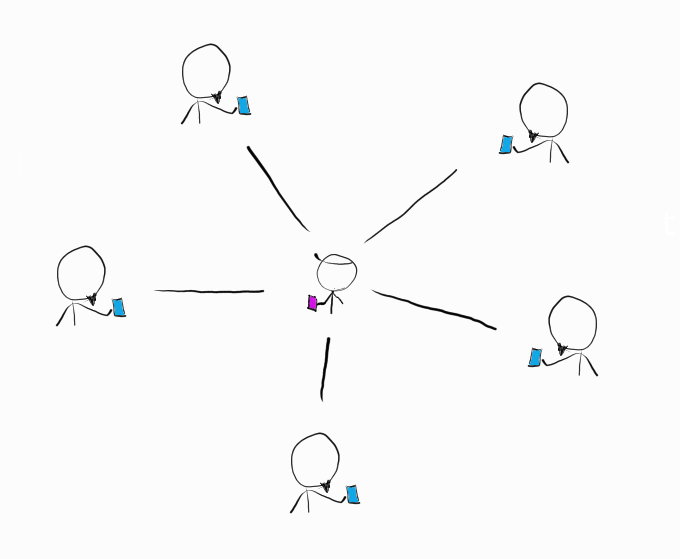
This is called a Sybil attack. Think of how one person can use multiple online identities to troll or attack people online; it’s hard to know who is real.
Proof-of-work
If you’ve heard about cryptocurrencies, then maybe you’ve also heard about cryptocurrency miners or Bitcoin miners. This is how Bitcoin provides sybil resistance and prevents double spends.
The core idea is: if you want to choose which transaction is valid you have to do work. The process is known as proof-of-work, shortened to POW.
The work is to find a solution to a computing problem. The problem itself is not that important, and it doesn’t have any meaning outside of mining. There’s some important properties it should have:
Hard enough
In Bitcoin, one solution is expected every 10 minutes. The difficulty is continuously adjusted to allow miners to join and leave.
An example is playing a game of Yahtzee, where the goal is to cast dice and get them all to have the same number, and you change the number of dice in play.
Easy to verify
While a problem should be hard to solve, it must be very easy to verify. It should be easy to verify on mobile phones, for example.
For instance while multiplying two prime numbers is easy, it can be very difficult to determine which two primes given only the product. This is used to make a type of public-key cryptography safe.
Memoryless
Knowing earlier outcomes shouldn’t give any advantage. Finding a solution should essentially be random.
It’s similar to how you’re just as likely—or unlikely—to get a Royal Flush on your first hand as on your 1000th hand. Whatever you got the other 999 hands doesn’t matter.
Cryptographic hash functions are excellent choices, Bitcoin uses SHA-256, for example. See the introduction to hashes for more details. For an in-depth explanation of Bitcoin’s proof-of-work, I recommend this post (2014), which shows how to mine Bitcoin with pen and paper.
A solution is proof that you’ve done the work—it’s proof that you’ve expended energy. It’s like a lottery and you can get lucky, but in the long run it balances out. Since you require a significant investment to find a block, this can be used as sybil resistance; you can’t just create thousands of fake identities for free.
It’s important to note that the system is permissionless so there’s nobody to prevent you from becoming a miner, but you also don’t have to be. The blockchain is open for anyone to read and validate, it’s only writing that’s exclusive to miners.
Updating the blockchain
When a miner finds a solution, she can update the ledger by adding a block to the blockchain. A block is basically a collection of transactions.
A blockchain is what it sounds like: a chain of blocks where a new block builds on previous blocks. When a miner searches for a solution, she must target a block on a specific height—the POW problem includes a reference to the previous block and it only fits at a specific position in the chain. When a new block is added, all miners need to work on a new problem targeting that block.
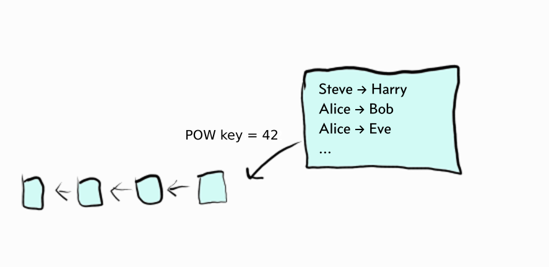
The transactions must follow common rules, called consensus rules, otherwise other miners and users who use the blockchain will discard the block. For example, a transaction cannot send coins from an empty address or spend coins without having access to the private key of that address.
In return for adding the block, you get to collect the rewards. One for finding a block, and you can collect transaction fees for the transactions you include in the block.
The blockchain is public and anyone can see all transactions. You can use a blockchain explorer to see for yourself; see for example the full history of this address or this transaction with one input and two outputs.
Cryptocurrencies, like Monero, that hide transaction amounts and the source and destination of coins also have a public blockchain, see this blockchain explorer, for example. While you cannot see what the transactions are doing, you can still verify that the transactions are valid and aren’t sending coins from empty addresses. The math on how exactly that works is outside the scope of this book—I can’t say I fully understand it either.
The blockchain is duplicated, stored, and maintained by many different people; you might think of it as similar to how torrents work. When you send and receive transactions, you’re really interacting with the blockchain and not with each other directly.
Forks
What happens if two miners find a block at the same height? For example, one where Sneaky Steve sends money to Honest Harry and one where Sneaky Steve sends money to himself?
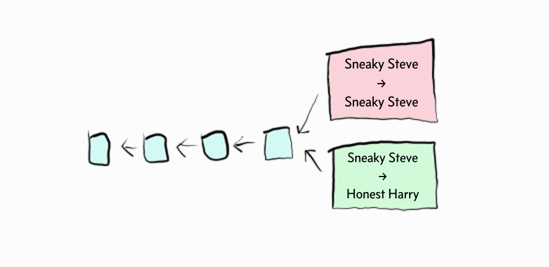
The chain will split, and there will be a fork. Each miner will independently choose which one they will build on and one will eventually become longer:
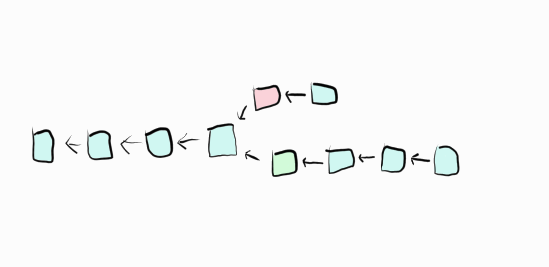
The longer chain is to be considered “the correct” chain and the shorter chain will be abandoned. Coming to consensus by following the longest chain is often referred to as Nakamoto consensus.
Because rewards on each chain can only be used on that particular chain, any rewards on the abandoned chain will be effectively worthless. Therefore, the miners are heavily incentivized to work on the longest chain and so the shorter chain will get abandoned quickly.
In the example, Honest Harry should wait until he knows which chain is longer and decide from there.
Reversing transactions
If Sneaky Steve can’t trick Honest Harry by showing him a fake transaction, he can try to reverse his payment after receiving goods from Honest Harry.
It works like this:
- Make a transaction to Honest Harry that’s confirmed on the blockchain.
- Create a longer hidden chain where Sneaky Steve keeps the money.
After receiving the goods, Sneaky Steve publishes the second chain.
Because people automatically follow the longer chain this effectively reverses the transaction to Honest Harry and Sneaky Steve has successfully commited fraud.
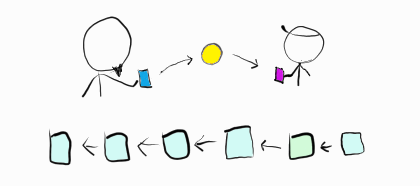


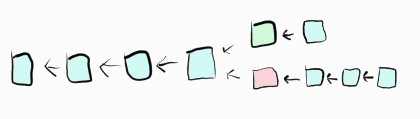
This is a different type of double spend, and it’s the primary attack vector the white paper is concerned about. It’s called a 51% attack, for reasons we’ll soon explain.
Transaction security
The deeper a transaction is in the blockchain—the more confirmations it has—the harder a transaction is to reverse.
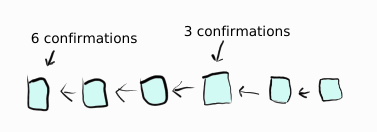
Each block added to the blockchain makes every existing block—and transactions—more secure.
Bitcoin’s security isn’t absolute but probabilistic. One way to think about it is to find one block you need to get lucky. To find more blocks you need to get lucky several times, which you have to do if you want to reverse a transaction with more confirmations.
Bitcoin’s white paper goes into more details and recommends 6 confirmations—roughly one hour—to be sure you don’t get defrauded. Today for most normal payments, a single confirmation is enough.
A crucial mistake people make is to think more miners, or more energy used, means more transactions can be handled. This is not true. Miners only care about securing the chain preventing transactions from being reversed.
In fact, we could spend 100x more energy on mining and process the same amount of transactions, or we could spend 1% of the energy and process more transactions. Transaction throughput is a separate problem.
The 50% security assumption
The whole system relies on a majority of miners being honest—it’s the core security assumption behind proof-of-work.
Honest miners work for profit so they absolutely don’t want to risk their blocks being rejected by the other miners and lose their reward. Therefore, the rational thing to do is to work on the longest chain.
This means for Sneaky Steve to successfully reverse a transaction he needs to control more than half of all mining power—otherwise his hidden chain can never become the longest. It’s called a 51% attack because you need to control at least 51% of all mining power to pull it off consistently.
This touches on the immutability of the blockchain. As long as more than 50% of miners don’t want to change the chain, it will always be longest and correct. But if they do then they can reverse transactions.
Economics of a 51% attack
How secure is Bitcoin, really? What do we need to pull off a 51% attack?
Here’s some quick napkin math to estimate the cost for 51% mining power:
| Total Bitcoin hash rate | 152,810,000 TH/s |
| Antminer S9i hash rate | 14 TH/s (+-5%) |
| Antminer S9i cost | $400 |
| Number of S9i to cover the whole network | 10,915,000 |
| Total network miner cost | $4,366,000,000 |
| Cost to reach 51% | > $2,183,000,000 |
So that’s more than two billion for just the miners themselves (assuming you could purchase that many—a big task as all miners are sold out!). On top of that, we need power supply, cooling, storage, and maintenance for millions of miners. We’re looking at a massive warehouse or several. Safe to say it’s a very large investment but maybe not impossibly large.
If we manage to get enough miners, it should allow us to double-spend and defraud exchanges and merchants. It almost sounds like we can get free money, but it’s not that simple.
A 51% can be detected and there can be severe negative consequences:
- The Bitcoin price might crash.
- Exchanges might blacklist the stolen funds.
- The community might change POW and make all mining rigs worthless.
- It’s hard to keep warehouses full of mining rigs of that scale a secret—there’s a big risk to get caught.
Bitcoin miners are rewarded in bitcoin and they also can’t be spent until after 100 blocks—roughly 16 hours. Executing a 51% attack that crashes the price would directly affect the rewards. If the community goes for the nuclear option and change POW, the massive initial investment into mining equipment might be lost.
These risks needs to weighed against what profits a 51% attack could generate. Maybe exchanges could get defrauded for $100 million (roughly a 5% return on investment)? A 51% miner would make that back in about one week—risk-free.
The economic incentives are so strong that it might be rational even for a 51% for-profit miner to be honest. In fact Bitcoin has had pools with 51% before without incidents.
The biggest security risk for Bitcoin might instead be state-level actors who wants to destroy it no matter the costs. For example if the United States would spend billions on a “War on Bitcoin”.
An economic innovation
While cryptocurrencies combine several different technologies in an interesting way, the real innovation is how they’re secured by economic incentives; that the most profitable way for miners is to follow the network rules.
As noted earlier, the current block reward for Bitcoin is 6.25 BTC, or around $250,000. Losing out on just one block reward is a big loss in the cutthroat mining business, so miners are heavily incentivized to always work on the longest chain.
For example, in a fork with two competing chains, the most profitable move is to jump to the longest chain as quickly as possible. This ensures that a double-spend gets resolved quickly.
It also doesn’t make sense for a minority miner to try to double-spend, it will only cause them to lose money in the long run. Therefore, only a miner with 51% can compromise the network security, and even then it may even be more profitable to play by the rules.
Network upgrades and new cryptocurrencies
There’s another situation where forks can arise: when consensus rules are changed. Here are some examples of consensus changes:
- Removing the 21 million supply cap in Bitcoin.
- Blacklisting or stealing coins from an address.
- Allowing a new transaction type.
- Tweaking the POW algorithm.
- Raising the 1 MB blocksize limit in Bitcoin.
Some cryptocurrencies, like Monero and Bitcoin Cash, have regular network upgrades where consensus rules are changed.
Because a network upgrade is a fork, there will be two chains (as long as someone mines them). Sometimes, the minority chain lives on as a new cryptocurrency; Ethereum Classic is the continuation of the old chain after an Ethereum fork.
Other times, the fork is initiated by people who want to create a new cryptocurrency from another one, but the mechanism is exactly the same. This means you can fork Bitcoin at any point if you want, the tricky part is getting other people to join you.
You may then wonder: what decides which is the correct chain? There’s no clear answer and social consensus decides which of the chains is called “Original Coin” and which is called “New Coin”. Social consensus may be very messy, and cryptocurrencies won’t help us there.
Alternative consensus models
There are alternatives to proof-of-work but none have so far been proven to work well. The most popular is proof-of-stake where instead of miners expending energy, you have coin holders who vote.
One problem is the nothing at stake problem where a coin holder can vote on all forks while a proof-of-work miner can only vote on one of the forks. It causes a situation where everyone is incentivized to vote on all forks, and an attacker can abuse it to reverse a transaction by only mining on their fork, which is initially a block behind, to overtake the main chain and reverse their transaction. This only requires a small percentage of total voting power in contrast to proof-of-work where you need 50%.
More details
In this chapter, I’ve focused on a high-level of understanding and I’ve skipped out on details occasionally. If you want to go deeper I encourage you to do more research on your own.
Bitcoin’s white paper is always a good place to begin, and there are also many good resources online. I’ve tried to include key concepts which you can use as starting points in your search.