Timestamping service
Verifiable proof of knowledge at a certain time
Bitcoin is an extremely important innovation, but not in the way most people think. Bitcoin’s real innovation is a globally verifiable proof publishing at a certain time. The whole system is built on that concept and many other systems can also be built on it. The blockchain nails down history, breaking Orwell’s dictum of “He who controls the present controls the past and he who controls the past controls the future.”
In How do cryptocurrencies work? we saw that cryptocurrencies work by preventing double spending coins, and the system chooses one of two potentially valid transactions. While doing so it also creates an order between blocks and transactions, which can be used as the basis for a decentralized timestamping service.
What is a timestamping service?
A timestamping service offers proof that a message or document existed at a certain time with certain contents. The idea of timestamping information is according to Wikipedia centuries old, dating back to at least the 17th century.
A modern example is the Wayback Machine, a service which allows you to see how a certain website looked at a certain time. A bit like traveling back in time, but with your web-browser instead of a DeLorean.
Let’s travel back in time and look at the site Hacker News, a tech oriented site where you can discuss news stores. I’ve lost a lot of time on the site reading insightful comments or getting upset at other less insightful comments.
| 1. | ▲ | Natalie Portman - Scientist (nytimes.com) |
| 100 points by mhb 2 hours ago | 43 comments | ||
| 2. | ▲ | Matt Blaze: How ACM and IEEE Shake Down Science (crypto.com) |
| 50 points by alterego 2 hours ago | 9 comments | ||
| 3. | ▲ | The Redis Manifesto (antirez.com) |
| 116 points by tednaleid 2 hours ago | 14 comments | ||
I tried to reproduce the site appearance, but it’s not pixel perfect.
As long as we can trust the Wayback Machine (and I do consider them generally trustworthy) we can be fairly sure this is correct. Letting a trusted party like the Wayback Machine handle timestamping, called trusted timestamping, is a solved problem with different kinds of standards but—as the name implies—there’s always the caveat of requiring a trusted party to verify the timestamps.
Usage examples
What is a timestamping service useful for? Here are some examples:
Proof of invention
Surprisingly often in history a discovery happens independently and at around the same time. What if you come up with an idea or an invention and you didn’t want to reveal it yet but still wanted to claim priority?
You would use timestamping. For example Robert Hook used it in 1660 when discovering Hooke’s law by publishing the anagram ceiiinosssttuv and later published the translation ut tensio sic vis (latin for “as is the extension, so is the force”).
Testaments
If you’re someone who likes to write testaments maybe you want to update the one you have. But after you die, how will people tell which is the newest? Sure you can write a date on the paper, but that can be altered by people who want the more beneficial one to be valid.
The solution is to use a timestamping service. If you use one based on a cryptocurrency there’s no possibility of altering the dates, not even by your lawyer.
Proving discovery of software bugs
What if you’ve discovered a major software bug and want to disclose it anonymously, but still want the ability to prove you were the one who found it? Later in the chapter we’ll go into details of how the discoverer of one of the most catastrophic bugs in Bitcoin ever accomplished this using timestamping.
Decentralized timestamping
With cryptocurrencies it’s possible to do away with the trusted party requirement and offer a decentralized timestamping service. We know that there’s no single trusted party that manages a cryptocurrency and instead many cooperate and reach consensus together. Therefore we only need to decide how to embed verifiable data and timestamps into a cryptocurrency:
Prepare data
Because we might want to reveal our message at a later date we don’t want to store the message in the clear. We can use an anagram like Robert Hook used, some kind of encryption with a key or a hash function to obfuscate the message.
After we have the obfuscated message we want to verify we can embed it into a cryptocurrency.
Retrieve timestamps
Transactions in an older block are older, transactions in a newer block are newer and transactions in the same block occur at the same time.1 You can observe, in a decentralized way, when a block with your transaction is created and use that as your message timestamp.
The blocks themselves don’t contain a trustworthy timestamp,2 but we can use the many different nodes observing the network to create an estimation. This could for example be the timestamps recorded by two nodes:
Block number Node #1 Node #2 #1001 2019-09-14 10:01 2019-09-14 10:01 #1002 2019-09-14 10:15 2019-09-14 10:27 ... #1007 2019-09-14 11:07 2019-09-14 11:08 A couple of blocks and their observed timestamps by two different nodes.
Blocks 1003–1006 are omitted.Here we see that the timestamps differ, at most by 12 minutes. Although not visible in the table the nodes tell us that blocks 1003–1006 happened some time between 10:15 and 11:08. We cannot be sure down to seconds or minutes, but it gives a good estimate if we’re only interested in an hourly or daily timestamp.3
This way we have the basis for a decentralized timestamping service. Insert an obfuscated message in a transaction and afterwards you can reveal the message and use the creation time of the block the transaction is included in as your timestamp. Also comparing two messages to find which the oldest is very simple: just check which block came first—there’s no need to look at a timestamp.
It’s much easier to use (I’ll go through an example step-by-step at the end of the chapter) compared to getting your message included in a publication like Hook did. You also don’t have to trust a timestamping service—the solution is fully opaque and you can verify it yourself.
A real-life example
One of the most catastrophic bugs in recent years, CVE-2018–17144, which if left unpatched would allow an attacker to print an unlimited amount of Bitcoin. It was found and disclosed by someone who at least initially wanted to stay anonymous, but he wanted the ability to prove he was the one who found it.
Therefore he decided to create this message:
BitcoinABC does not check for duplicate inputs when processing a block,
only when inserting a transaction into the mempool.
This is dangerous as blocks can be generated with duplicate transactions
and then sent through e.g. compact block missing transactions and avoid
hitting the mempool, creating money out of thin air.
/u/awemanyWhich has the SHA-256 hash:
5c45a1ba957362a2ba97c9f8c48d4d59d4fa990945b7094a8d2a98c3a91ed9b6And inserted it into the BTC blockchain using a timestamping service. See “Advanced Verification” on the website to find the hash and see the explanation of hash functions for why the hash is enough.
This proves that reddit user awemany had knowledge of the inflation bug before it was disclosed and therefore that he was the one who found it.
Please read his writeup of how he found the bug and the related discussion on reddit for more info.
We can do it ourselves
The previous example used a timestamping service which did the conversions for us, but it’s actually easy to do everything ourselves.
Let’s say we want to obscure and timestamp the message Hook used:
as is the extension, so is the forceLet’s now encode and timestamp it using the Bitcoin Cash blockchain:
Encode the message using SHA-256
On Linux we can run the command:
echo -n "as is the extension, so is the force" | sha256sumGiving us the SHA-256 hash:
dab965bb19823669b8481846b9672c694a9af1b808314956b43154a0472942d8Insert it in a transaction using OP_RETURN
For this step you need a wallet capable of creating a transaction with a custom OP_RETURN field, I used the desktop version of Electron Cash 4.0.14 and enabled the OP_RETURN field in settings. You need to have enough money to pay a small fee and use a small amount to transfer.
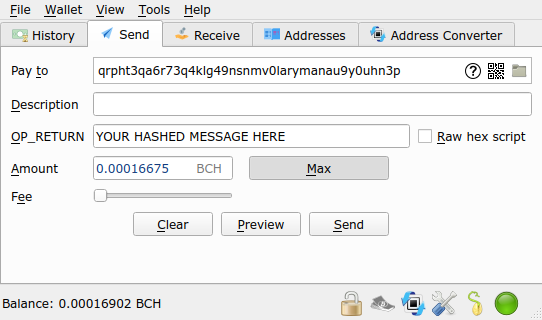
Custom OP_RETURN using Electron Cash. We can double-check the transaction on a blockexplorer, such as Blockchair, to see that the OP_RETURN value matches our SHA-256 hash (look for the decoded OP_RETURN field).
With that our timestamp is prepared and nobody can see our original message, only the SHA-256 hash. When we’re ready to reveal our message to the world, all we have to do is show everyone the message and how to verify the timestamp:
Locate the hash in the blockchain
It’s probably easiest if we point out which transaction we’ve included our hash in. This is the txid:
586783e17fadace136365490fd83ba59390ca55e7205ee74fbc7db2daa012ad3Here’s the same transaction using another blockexplorer.
Verify the SHA-256 hash
The message should encode to the the same hash that’s included in the blockchain.
Lookup the timestamp
According to Blockchair the transaction was included in a block mined 20:17 September 15, 2019 (UTC). Verifying the timestamp with other blockexplorers or full nodes is left as an exercise to the reader, just be cautious of timezone differences.
We now have a trusted timestamp for our message, backed by math instead of trust.
